You Have Cryptographic Keys in the Wild
We Help You Find Your Cryptographic Vulnerabilities Before They Do
Do You Know Your Cryptographic Posture?
Cryptography is used to protect our most sensitive secrets, systems, and data. However, cryptographic vulnerabilities are the Achilles Heel of our cyber defenses. The reason for this is because government agencies are unable to identify and manage cryptographic keys that are outside of their visibility and control –what we refer to as “Keys in the Wild.”
The threat is real. Solarwinds, Storm 0558, and other successful devastating cyber-attacks exploited cryptographic vulnerabilities. NSM 10 and OMB 23-02 are attempts by the U.S. Government to drive agencies to identify and shore up these vulnerabilities by requiring agencies to conduct a comprehensive inventory of their cryptographic assets. However, most agencies do not know how to go about conducting an inventory.
It is now a race against adversaries to discover and inventory all cryptographic assets – particularly keys in the wild – and to prioritize risk, and remediate vulnerabilities before adversaries wage attacks against them.
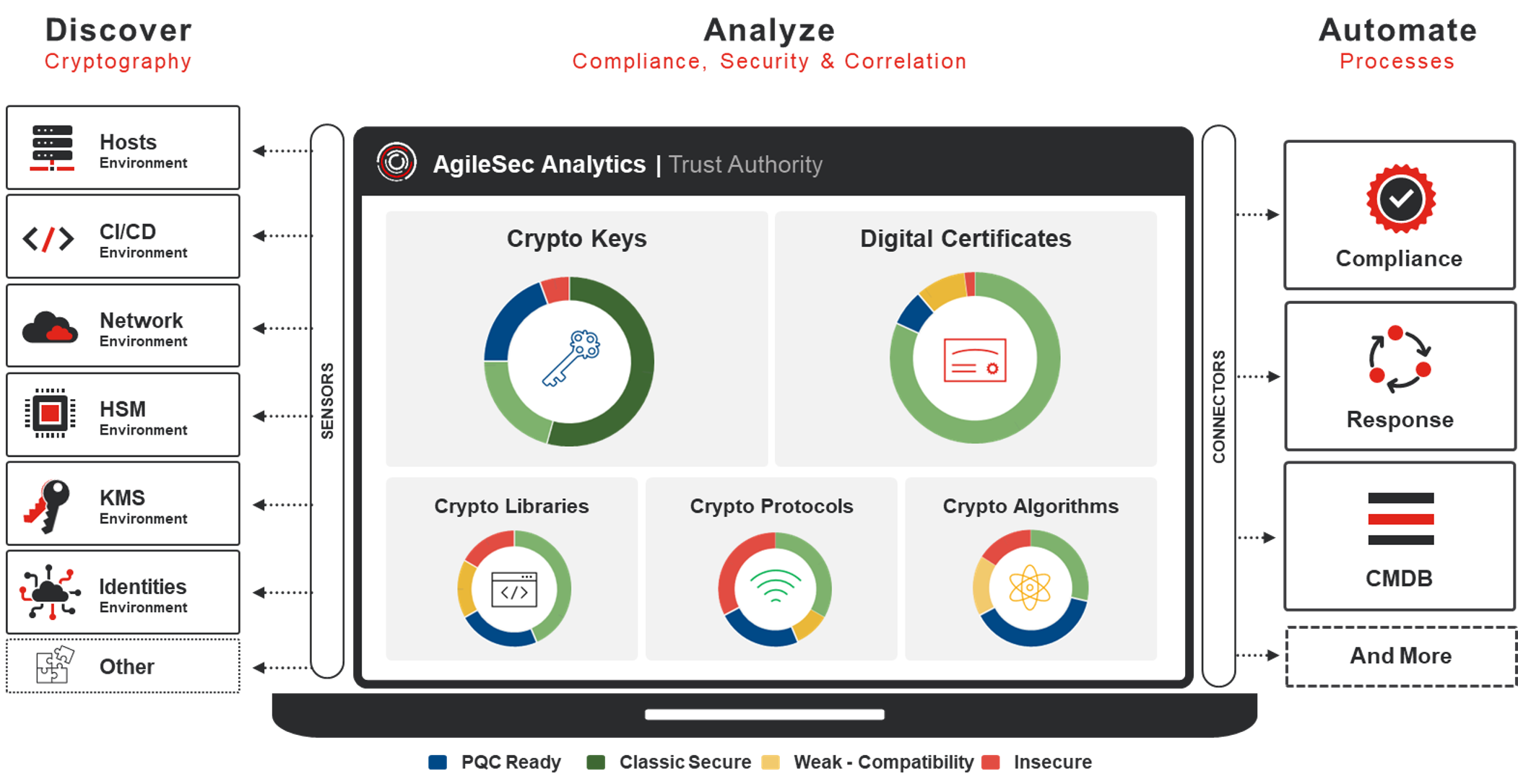
Discover, Inventory, and Remediate Your Cryptographic Assets with Ease
InfoSec Global Federal provides an easy, non-disruptive solution to help agencies inventory, manage, and control all of their cryptographic assets. With AgileSec Analytics®, agencies can discover keys in the wild and present a comprehensive inventory.
Get Started: Pilot Up to 250 Hosts
We’ve made it simple for agencies to see how AgileSec Analytics works. We will discover keys in the wild that you never knew existed – equipping you with invaluable risk insights and inventory to help you answer the call for cryptographic asset inventory, understand your cryptographic posture, and reduce risk.